|
|
| Home - Industry Article - Apr 07 Issue |
Intelligent Protection: Document Security for Your Data in Motion |
By Dave Malmstedt, CEO, Vincera, Inc.
The need to secure data in motion – not just data at rest – has never been more pronounced than it is today. The speed of business in the Information Age has made it not only possible but also necessary to e-distribute intellectual property, personally identifiable information and other privileged information via documents. Ironically, the very tools that have energized information distribution have created fresh vulnerabilities for our companies. Arguably, today your mobile ‘secret’ documents, such as PDFs, are more prone to theft, alteration, and illicit use than ever before.
Protecting Your Data In Motion – Documents – to Reduce Corporate Losses
Yes, corporate espionage has gone digital, and the results are very real! Although most corporate executives remain unaware of the scope of damage, estimates place up to 35% of lost corporate revenues arising from the illicit distribution of documents (KPMG, 2005). And immediate economic loss isn’t the worst of it. Your greatest damage can be to your brand (Gartner, 2005).
Yet, with the right distributed-document security strategy, these economic and brand losses can be minimized or eliminated.
The Challenge: Secure Your Data in Motion and Maintain the Speed of Business
While the need to secure enterprise information is real and the appreciation for that need is real, there is also an apparent lack of appreciation on the part of the enterprise regarding the scope of the challenge.
When queried about the problem, most information security professionals immediately emphasize static data security and measures, but neglect corporate documents and their inherently mobile nature. InfoSec professionals say it’s the data that must be protected; then they explain all the measures being put into place to secure access to the enterprise, to strengthen the firewall, to make the databases literally inaccessible, and how access to this data is allowed only to those fully authenticated by access procedures. It’s a ‘circle the wagons and don’t let anybody in’ security schema.
Yet this approach fails to acknowledge two essential facts: First, your company’s sensitive data reside primarily in documents that are distributed beyond your corporate firewall; database security does not address this vulnerability. (See below.)
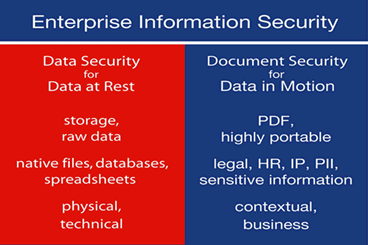
Not all data are stored in a database or a spreadsheet. In fact, data that support the business are very mobile and reside primarily in documents.
Second, traditional means of document security (i.e., traditional DRM) are terribly cumbersome and hinder the mandatory speed of business.
Truth be known, the #1 impediment to implementing information security is the need to conduct business! And a great barrier to conducting business expediently has been the traditionally unwieldy DRM solutions.
Thus, InfoSec professionals face a challenge that, until now, has been somewhere between monumental and insurmountable: to protect all important, sensitive data in motion while maintaining the necessary speed of business.
The image below encapsulates the difficulties inherent in meeting this challenge. In virtually all businesses, sensitive documents are routinely routed between multiple data sources and recipients. And although a corporate firewall typically exists, this measure does nothing to protect documents once they have reached legitimate recipients.
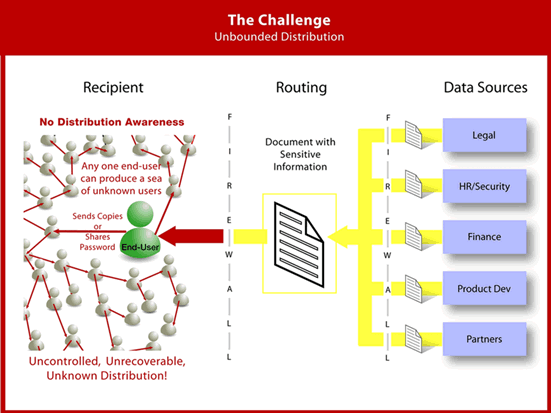
The Current State: Unbounded Distribution
What happens to your sensitive data in motion today?
Uncontrolled, unrecoverable and unknown distribution. For most digital documents including Adobe PDF, free or cheaply available equipment and software exist to reproduce exact copies of unprotected content. And the only gatekeepers for most e-distributed documents are easily shared login names / passwords. All it takes is one legitimate employee or customer to set off an unknown chain reaction of uncontrolled and unauthorized distribution.
“One instance of brand damage due to a security breach can destroy a company – who takes the blame?” Gartner 2005
What about traditional digital rights management (DRM)?
Traditionally available digital rights management (DRM) solutions allow you to select from the outset, specifically who may use specific files. DRM’s authentication takes place at the front end, tying a specific named document to specific named users. With traditional DRM, there might be a different set of permissions for every document and user. The problem arises when it’s desirable from a business standpoint to allow others to access the document; traditional DRM makes adding another user quite labor-intensive, requiring that every user who desires access to a specific document be given the explicit right to do so. Although this approach is feasible for highly confidential documents, it is prohibitively cumbersome for the majority of enterprise documents that are less sensitive and require distribution.
Thus, this complex, management-intensive and inflexible access control scheme becomes cumbersome as you need or desire to add new, legitimate persons and machines to your document-sharing network, and as the content in documents requires update or expiration.
Consequently, DRM can take years to implement across enterprises and tends to negatively impact the normal information distribution flow to authorized recipients within an organization or partner base.
In short, traditional DRM solutions drastically slow the necessary speed of business.
For example, it may be easy to identify and maintain the list of authorized recipients of a document within a small workgroup. This becomes more complex if the size of the group becomes a several hundred-person department. And there are multiple ‘rights’ that can be granted to various persons. This gets more complex when the group is distributed and encompasses several departments, other enterprises, other enterprises’ partners, and so on. The ‘speed of business’ becomes the speed of an administrator to add a new recipient of the document who is a partner of your partner – yet they must approve the product changes by noon today in order for you to meet your production schedule.
Hence, traditional DRM often falls out of use or is never implemented, and the distribution of corporate secrets in document form continues to be subject to the whims of the recipient.
In our interactions with InfoSec professionals in diverse industries, the complaints we have heard regarding DRM are numerous:
- “I’ve been working on implementing DRM in my company for 2 years and it still isn’t fully implemented.”
- “We implemented DRM, but it is used by only a few pockets of people in our product development area. It’s too hard to leverage it in the business units.”
- “Implementing DRM wasn’t as hard as maintaining and managing the use.”
|
|


|

